The Basics of Wi-Fi Security
To avoid security breaches and other dangers, you need to set your network up securely. It isn't very hard, and this guide will explain what you need to do.
Home WiFi access points are tremendously useful and popular. They let you set up your network without running cables. You can put devices wherever they're convenient and make phones and tablets part of the network.
When you do this, though, you have to think about the security issues. If you do it carelessly, outsiders can get into the network. They can get to your computers and other devices. An intruder might even take control of your router.
The Risks
If you leave your network wide open, anyone within range can access it. If it's your neighbor next door doing it occasionally, it may not be a problem. But it could be someone using the Internet for illegal purposes. Whatever they do could be traced back to your IP address, and you could end up having to explain to law enforcement that it wasn't you.
An open network is subject to "evil twin" attacks. Someone else can set up an access point with the same name. Devices set to automatically connect to your network may connect to it by mistake. The rogue access point could record and even alter the traffic that goes through it.
There are risks to your own network. Someone who connects without permission can bypass security measures such as the router firewall. This might let them put malware on your machines or access private information.
An attacker who gets into your router's admin account can change its settings, removing firewall protections and changing domain routing. The result could be ongoing harm that you aren't aware of.
WiFi In Your Home Network
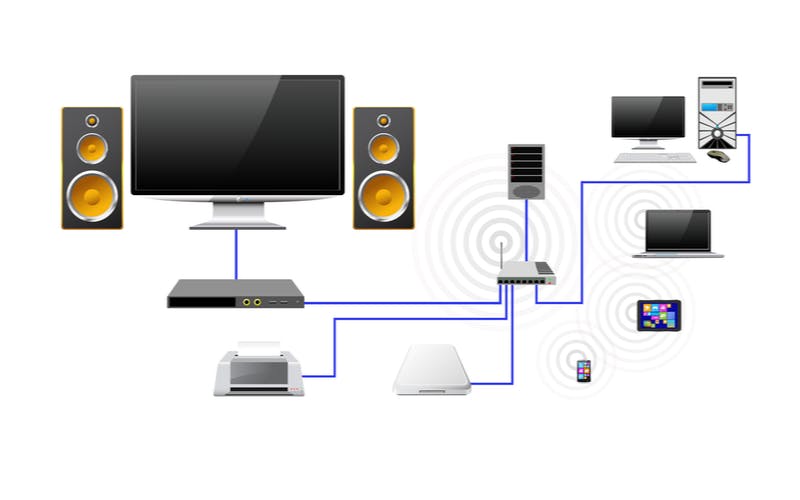
The equipment connecting your systems to the Internet generally includes a modem, a router, and one or more WiFi access points. They might all be in the same unit or in separate boxes. It's common for a router to include Wi-Fi capability. You might want an additional access point for better coverage.
For this discussion, we'll talk about the Wi-Fi part as an access point, whether it's part of another device or a separate unit.
The equipment comes with factory settings that are the same for every unit of a given model. If you leave it as it is, you present a target that everybody knows about. That signals that you haven't taken the trouble to configure it, suggesting that you could be easy pickings. For the best router security, you need to do some customization.
Understanding WiFi Protocols
Wireless communication with WiFi is defined by the IEEE 802.11 standard. It's gone through many editions. Each one has a one or two-letter identifying suffix.
The Wi-Fi Alliance has adopted a new scheme, which is easier to understand than the chaos of suffixes. The current generation, described by 802.11ac, will be known as WiFi 5. The next generation will be called WiFi 6, which is based on 802.11ax. Not many people have heard of this terminology so far, but it will be used everywhere once WiFi 6 equipment hits the mass market. Major revisions of WiFi come out about every five years.
The SSID
Every WiFi access point has a service set identifier, or SSID. It's the "name" of the unit and can be as many as 32 characters long. The manufacturer provides a default SSID. It isn't unique, and there's no way to prevent someone from using the same SSID as a given access point. How do you make sure you're connecting to the right one? The answers WiFi offers aren't as good as they might be.
Encryption Options

Wi-Fi traffic goes over the air using well-known protocols. Anyone can intercept it with off-the-shelf equipment. If it isn't protected, they can see what you're sending and receiving. Fortunately, Wi-Fi offers protocols which encrypt traffic between devices and access points. If you're using a secure Internet connection, that information is protected, but a lot of traffic consists of unprotected data. With an unencrypted wireless connection, information is exposed to lurkers.
A public connection, such as one at a shopping mall or library, has no encryption. This creates a risky situation. Someone else can set up an access point with the same SSID. That is known as an "evil twin." Clients may connect to it, thinking they're using a trusted connection. While an unencrypted access point takes the least effort, it's a bad idea. Public facilities use it because they have no choice, but you shouldn't set your home network up that way.
WEP
The oldest of the WiFi security types is WEP. It supposedly kept communication private, but several serious flaws were discovered in it. With modern levels of computing power, it's not extremely difficult to crack. It's an obsolete protocol, and you shouldn't use it in your network.
WPA
The Wi-Fi Alliance replaced WEP WiFi encryption with a protocol called WPA. The first version came out in 2003. While it was much better than WEP security, the original WPA had significant weaknesses. It was replaced by WPA2 in 2006.
WPA2
WPA2 is currently the best protocol available for secure WiFi connections. A significant weakness turned up in 2017, though. It's called the KRACK, or "key reinstallation attack," vulnerability. It can be used to eavesdrop on communications and even to alter data with a "man in the middle" attack. The vulnerability is inherent in the protocol, but the implementation can mitigate it. Most current devices have updates that remedy the KRACK weakness. Old devices that haven't had a firmware update in years are likely to be susceptible to it.
WPA3
A better encryption protocol, WPA3, is on the horizon as part of WiFi 6. It offers better security, stronger protection against password guessing, easier connection for IoT devices, and encryption for public access points. If both ends of a connection don't support it, it will fall back to WPA2. Devices supporting the new protocol should be widely available by the end of 2020.
How To Improve Your WiFi Security

Several concrete steps will make your network's WiFi safer against penetration attempts.
- First, change your SSID from the default to a distinctive name. This will reduce mistaken connections if a nearby device uses the same factory default. You can call it something clever, like RebelBase1, but avoid putting real information such as your name into it. There's no point in giving strangers clues about your network.
- There's an option to have your access point not broadcast its SSID. This means it won't show up on a list of access points within range of a device. It really doesn't help much. A client has to broadcast the SSID when searching for it, so the name isn't secret. It isn't worth the trouble.
- What is useful is to have different SSIDs for owner and guest access. With devices that offer this, only the owner can access the settings, including router settings. If you want visitors to have access, you need to give out the password. Even if you trust them, someone you shouldn't trust may get hold of it. If you need to change the guest SSID, you can do it without disrupting your own network usage.
- For encryption, use WPA2, When WPA3 is available, you can switch to it, and WPA2 devices will still be able to use your access point. This prevents "evil twin" attacks, since the other access point won't know your password. (A client device doesn't send the password to the access point, but instead performs a handshake that requires knowing it.)
- If you have a wireless router, it will have an admin account. The user name is usually "admin" or "administrator." Change it to something else to make it harder for intruders to break in. Log in to the account and check the dashboard occasionally, to make sure nothing amiss is happening. When you're done, log out.
- Check regularly for firmware updates to your access point or router. You may be able to set it to check and install them automatically. This saves you from forgetting. Updates may fix important security issues.
If you do everything mentioned so far, you're in good shape for wireless security. If you want to go for a little more, here are some additional suggestions.
Pro Tips
- If you won't be using the access point for an extended period, turn it off and unplug it. Having it shut off while you're on vacation will keep it safe from attacks, as well as saving a little energy and protecting it from power surges.
- Review your router firewall settings and customize them to protect your network. If there are any types of connections that you never use, disable them. The smaller your attack surface is, the safer the network is.
- If your access point or router offers remote administration, you should turn it off unless you really need it. There's no sense in giving someone a chance to log in to your router over the Internet.
Understanding Your Network
Take some time to understand your wireless network, and you'll be able to protect it better. You should know what all the devices on it are and be able to identify their IP addresses. We offer a tool to identify your router's IP address. If you spot devices that shouldn't be there, check where they're coming from and whether they should be there. If you've got questions or comments, feel free to contact us.