Comparison of VPN Protocols: OpenVPN, WireGuard, IPSec, L2TP, and IKEv2
In this post, we'll briefly take a look at what a VPN is for those who don't know or who only have a vague idea. Afterward, we'll take a look at how the most common VPN protocols work. Finally, we'll give you some tips on choosing the right VPN protocol to protect you and your internet traffic from unwanted snooping.

It's common these days to see advertisements for VPNs that promise to protect your anonymity and security on the internet. These tools have gone from being used mostly by businesses to finding a large consumer-level user base. This change has no doubt been driven by the amount of spying and other malicious behavior that has become an all too common part of the internet experience.
What is a VPN?
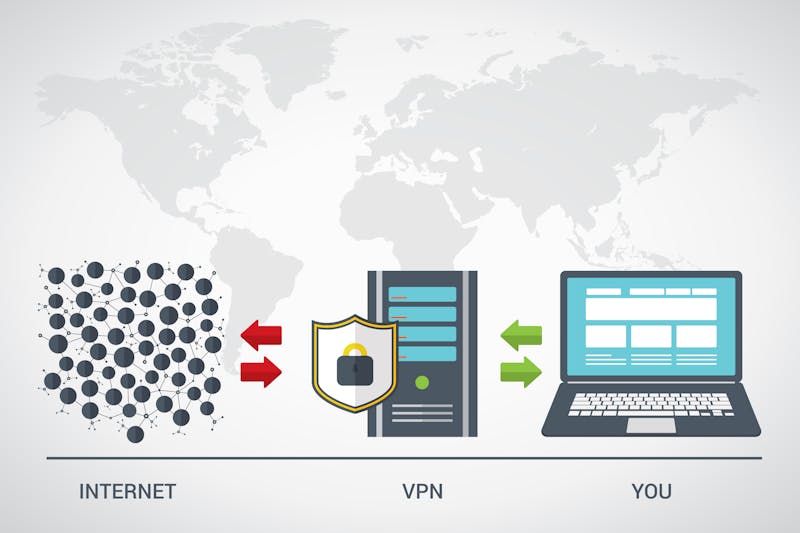
VPN stands for 'virtual private network'. Without a VPN, your IP address follows you everywhere. Every site you visit can see this IP address and your internet service provider can trace the IP address back to you. There is no privacy, there is no anonymity. With a VPN, you are essentially connecting to the internet through someone else's internet connection. This means that instead of your real IP address, traffic from you will appear to come from another IP address.
This masking of your IP address aids in your privacy because it stops spyware from knowing exactly who you are. In some countries with strict internet censorship, a VPN can help users get past the protections and out to the larger internet. This works because they are technically connected to the internet from the country that the VPN server is at. Your request for an internet page will travel to the VPN before getting sent out to the requested page. The data will come in through the VPN before being sent to you. All of this happens through an encrypted connection for increased security.
The way in which a VPN sends internet packets back and forth, called tunneling, and the way that it encrypts the data are the two factors that make up a VPN protocol. There are several protocols that are used for connecting to a VPN. Let's take a look at some of them.
OpenVPN

Being free and open-source software has made OpenVPN one of the most used VPN protocols in the world. Its open-source nature means that anyone with programming experience can take a look at the source code and confirm for themselves that nothing malicious is going on. It also means that security vulnerabilities are discovered and patched quickly, resulting in OpenVPN being one of the most secure VPN protocols in common use.
Most computers don't come with OpenVPN installed, so users need to download and install it themselves. This is a simple process and there are OpenVPN clients available for all major operating systems across both the desktop and mobile spaces. This gives a great advantage to people paying for a VPN service that uses the OpenVPN protocol because the service will work with whatever machines the user has without relying on the VPN company to provide support for every operating system.
The protocol uses the OpenSSL library for encryption. This brings with it two major advantages. First, the protocol works fine with existing web browsers so that your VPN usage can be as seemly as possible. Second, Open SSL supports a wide variety of encryption options, including some of the most powerful encryption algorithms available today, such as the military-grade AES-256 algorithm.
Because traffic has to travel to the VPN and back as well as to the internet and back, VPN services can be slow. OpenVPN is one of the fastest protocols available. TCP is the most commonly used packet transfer protocol on the internet but requires a lot of error checking that can slow it down relative to the other common protocol, UDP. OpenVPN allows you to choose either of these two protocols to handle the sending of its packets. UDP will provide greater speed, but if packet loss becomes a problem, TCP will provide more reliability. TCP can also be made to look like regular internet traffic, making the VPN harder for your ISP to block.
Pros:
- Works with any operating system
- Fast
- Secure
Cons:
- Requires additional software
WireGuard
A new open-source competitor to OpenVPN is under development in the form of WireGuard. The protocol shows some promise for becoming the fastest of the VPN protocols but is still very early in development so all of the features that a VPN provider would want to provide are not in place yet, putting the responsibility on the service provider to fill in the gaps. As the project matures more, that will no longer be a problem, but there are still some concerns about WireGuard that may limit its ability to fully replace OpenVPN as the top dog in the fight.
WireGuard supports UDP but does not support TCP. Generally speaking, lost packets aren't a huge problem for VPNs so the lack of TCP doesn't necessarily present a technical problem, but it does make it easier to detect as VPN traffic and block. Because the protocol is so new, it has not been audited for security and currently should not be used when that may be an issue.
One big advantage that the protocol will bring over its speed boost is that it will allow users to more seamlessly switch their network connection without interrupting the service and will reconnect faster if service is interrupted. This is of special interest to mobile users, who may frequently switch between mobile data and Wifi.
Pros:
- Fast
- Handles network switching well
Cons:
- Not a completed project
- Untested security performance
- Doesn't support TCP
IPSec

Internet Protocol Security (IPSec) was developed by the Internet Engineering Task Force. The goal of IPSec is to serve as a network communications protocol that encrypts the data being communicated. In that sense, it is similar to SSL. The key difference between IPSec and SSL is that IPSec works at the operating system level, rather than at the application level. This means that as long as your operating system supports it, you can run IPSec VPNs without having to download any additional software.
Security of IPSec has been called into doubt because leaked NSA documents have hinted at the fact that the agency has cracked IPSec security. While it is still considered secure when set up properly, those using VPNs to avoid government detection may wish to use another protocol.
IPSec is also used as the encryption in two other VPN protocols. These protocols aim to improve the tunneling aspect of IPSec while taking advantage of its security features.
Pros:
- Builtin to the operating system
- Fast
Cons:
- Possible security issues for certain uses
L2TP

Layer 2 Tunneling Protocol (L2TP) is one of the two VPN protocols that pairs with IPSec. Like IPSec, it is supported at the operating system level by several operating systems and can, therefore, be used without having to install any software. Individual VPN providers will give their users configuration files that can be sent to L2TP and IPSec in order to facilitate the connection.
The protocol itself does not provide any encryption functionality, which is why it is paired with IPSec. It is based on two older protocols, Layer 2 Forwarding Protocol by Cicso, and Point to Point Tunneling Protocol by Microsoft. The proprietary nature of the code means that you must put your trust in the developers since an independent review of the source code is not possible.
L2TP functioning at the operating system level means that it can, in theory, do its job faster than a protocol that operates in application space. However, L2TP uses some of that extra speed to double encrypt the data. This provides extra security, but at the cost of speed.
Pros:
- Builtin to the operating system
- Double encryption
Cons:
- Might not work on all platforms
- Not as fast as IKEv2
IKEv2

Cisco and Microsoft worked together again to create IKEv2. The first version of the Internet Key Exchange (IKE) protocol came out in 1998 and was followed up in 2005 by IKE version 2. Although it suffers the same downside as L2TP of being closed source, it is widely considered one of the fastest and most secure VPN protocols available. The speed of IKEv2 particularly shines when reconnecting, which makes it a good choice for mobile users for the same reasons mentioned for WireGuard.
As it is also built on IPSec, IKEv2 is supported at the operating system level and enjoys broad support across most common operating systems so it is easy to configure and does not require users to install any special software.
Pros:
- Builtin to the operating system
- Fast
Cons:
- Might not work on all platforms
Choosing the Best Protocol
Ultimately, the protocol you choose will be based on your needs. Businesses that want to maintain as little software as possible would do well with IKEv2. Since it is built into the operating system, it is one less application that needs to be updated and maintained by an IT staff. Consumers may find OpenVPN the better option. It is a common protocol that is easy to install, fast, secure, and well supported among the various VPN providers. WireGuard is worth keeping an eye on, as it may become a strong contender in the future, but is best avoided for now.
If you found this article informative, we invite you to look around at the rest of our blog posts. We try to produce great content that helps to answer all of your tech questions. If there's something you'd like to see us cover, contact us and let us know.